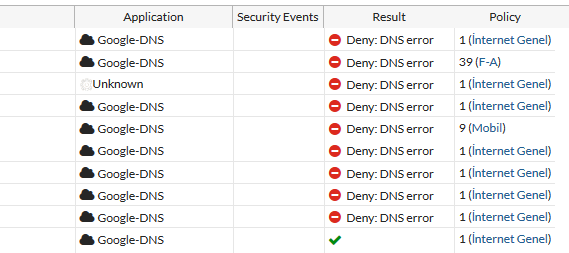
Herkese Merhaba, Fortios 5.4.1 ile gelen bir hatadan bahsedeyim. Bulunduğunuz ortamda internet yavaş şeklinde şikayetler alıyorsanız ve speedtest e girdiğiniz de Bant genişliğiniz kadar hız görebilirsiniz fakat speedtest yavaş geliyorsa yinede log lar alttaki gibi olacaktır. Action kısmında Deny:DNS error ...
Archives
Host Dosyasına Kayıt Ekleme
GPO Account Password Ayarlarını Değiştirmek
IIS Server da Process Sayısını Arttırma
Fortigate 5.4.X DNS Sorunu
IIS de Site ve AppPool İmport/Export işlemi
IIS Server da Process Sayısını Arttırma
Fortigate SD WAN Nedir ? Nasıl Kurulur ?
Fortigate Multiple İnterfaces Policies Nedir ?
SQL Server ve Perform Volume Maintenance Task
Fortigate LDAP Authentication
The Hacker News
- North Korean Hackers Deploy New Golang Malware 'Durian' Against Crypto Firmsby [email protected] (The Hacker News) on 10 Mayıs 2024 at 14:54
The North Korean threat actor tracked as Kimsuky has been observed deploying a previously undocumented Golang-based malware dubbed Durian as part of highly-targeted cyber attacks aimed at two South Korean cryptocurrency firms. "Durian boasts comprehensive backdoor functionality, enabling the execution of delivered commands, additional file downloads and exfiltration of files,"
- CensysGPT: AI-Powered Threat Hunting for Cybersecurity Pros (Webinar)by [email protected] (The Hacker News) on 10 Mayıs 2024 at 12:52
Artificial intelligence (AI) is transforming cybersecurity, and those leading the charge are using it to outsmart increasingly advanced cyber threats. Join us for an exciting webinar, "The Future of Threat Hunting is Powered by Generative AI," where you'll explore how AI tools are shaping the future of cybersecurity defenses. During the session, Censys Security Researcher Aidan Holland will
- Chrome Zero-Day Alert — Update Your Browser to Patch New Vulnerabilityby [email protected] (The Hacker News) on 10 Mayıs 2024 at 10:23
Google on Thursday released security updates to address a zero-day flaw in Chrome that it said has been actively exploited in the wild. Tracked as CVE-2024-4671, the high-severity vulnerability has been described as a case of use-after-free in the Visuals component. It was reported by an anonymous researcher on May 7, 2024. Use-after-free bugs, which arise when a program
- What's the Right EDR for You?by [email protected] (The Hacker News) on 10 Mayıs 2024 at 10:22
A guide to finding the right endpoint detection and response (EDR) solution for your business’ unique needs. Cybersecurity has become an ongoing battle between hackers and small- and mid-sized businesses. Though perimeter security measures like antivirus and firewalls have traditionally served as the frontlines of defense, the battleground has shifted to endpoints. This is why endpoint
- Malicious Android Apps Pose as Google, Instagram, WhatsApp to Steal Credentialsby [email protected] (The Hacker News) on 10 Mayıs 2024 at 10:21
Malicious Android apps masquerading as Google, Instagram, Snapchat, WhatsApp, and X (formerly Twitter) have been observed to steal users' credentials from compromised devices. "This malware uses famous Android app icons to mislead users and trick victims into installing the malicious app on their devices," the SonicWall Capture Labs threat research team said in a recent report. The


Son yorumlar