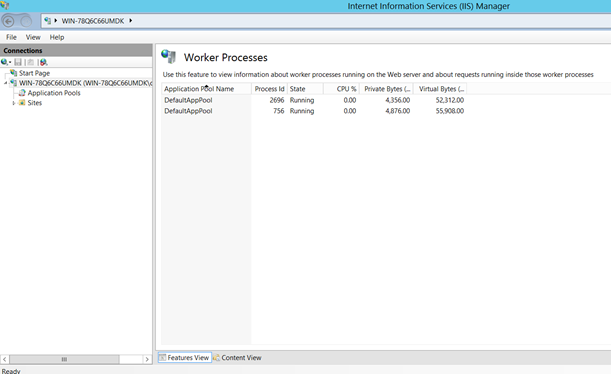
Herkese Merhaba, Bu yazımızda IIS server da App Pool daki proceslerin sayısını artırmayı göstereceğim. Öncelikle tabiki neden böyle bir şey yaptığımızdan da bahsedelim hızlıca; Konumuz şu 1 tane uygulamamız var web sitesi olsun yada başka bir servis farketmez. IIS in ...
Author Caner Aktaş
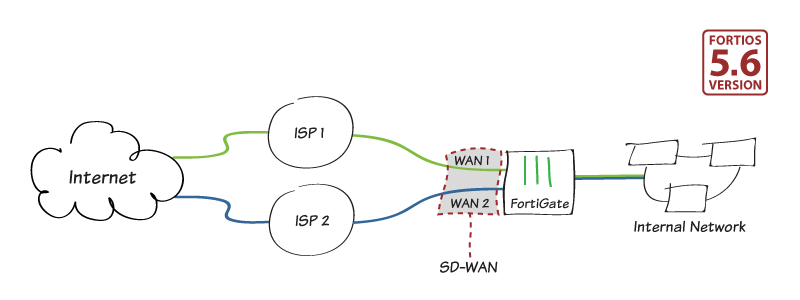
Herkese merhaba öncelikle bugün size SD-Wan üzerinde konuşacağız. Internette bir sürü bununla ilgili makale var özellikle Fortigate SD Wan ile ilgili baya bi kaynak mevcut bu konuya biraz derinlemesine anlatmalıyım diye düşündüm ve istek üzerine yazayım dedim. Öncelikle SD Wan ...
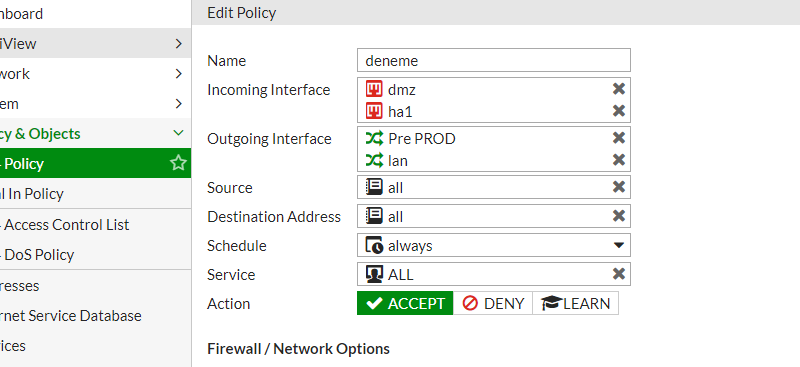
Herkese Merhaba, Fortigate’ in Multiple İnterfaces Policies özelliğinden bahsedeceğiz. Ne işimize yarar diye düşünürsek normalde source ve destination interface eklediğimiz kuralları düşünün ve onu sources ve destinations olarak değiştirelim kısaca kural kalabalığından kurtarıyor diyebiliriz. Dezavantaj olarak ise (makalenin sonunda farkı ...
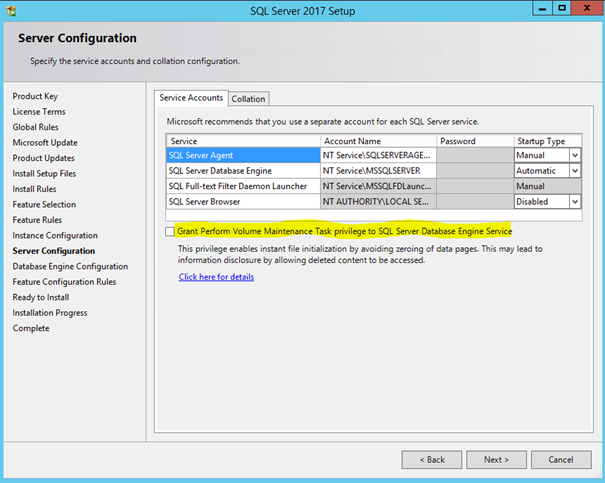
Merhaba arkadaşlar, Bugün daha önce SQL Server 2017 Kurulumunda kısaca bahsettiğim ‘Grant Perform Volume Maintenance Task Privilege to SQL Server Database Engine Service’ den bahsedeceğim. Şimdi SQL server kurulumu yaparken bu seçenek tik li gelmez yani opsiyoneldir. Önceki versiyonlarda SQL ...
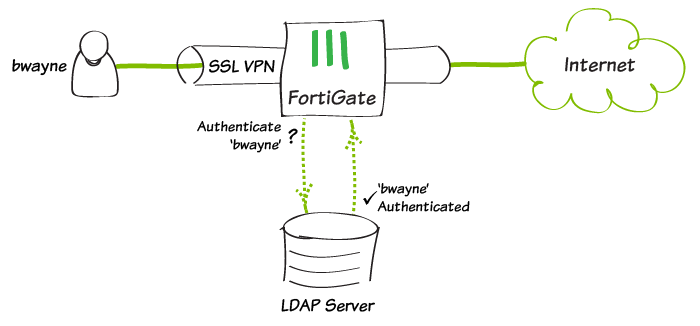
Merhaba arkadaşlar, Bugün Fortigate 5.47 build de LDAP Authentication nasıl yapılır onu anlatacağım. Adımları kısa tutup detaylara ağırlık vereğim. Menü den User & Device > LDAP Servers tabına geliyoruz. Ve Create New diyerek üstteki ekrana ulaşıyoruz. Bu ekranı alttaki gibi ...
Merhaba arkadaşlar, SQL Server kurulumu ile ilgili binlerce makale arasından birine daha hoşgeldiniz. Bu makalede SQL Server 2017 kurulumunu anlatacağım ve birkaç trick noktaya değineceğim. Bilmeniz gereken ilk şey SQL server 2017 ile beraber Management Studio ile SQL Server birbirinden ...
Merhaba arkadaşlar uzun bir aradan sonra güzel bir bilgiye değinmek istedim. SNI daha önce duymuş olabilirsiniz açılımı Server Name İndicaiton dır. Dibine kadar açıkla lan diyenler için LİNK ekledim VPN açıp bakabilirsiniz J Kısaca özetlemek gerekirse yıllardır süre gelen IIS ...
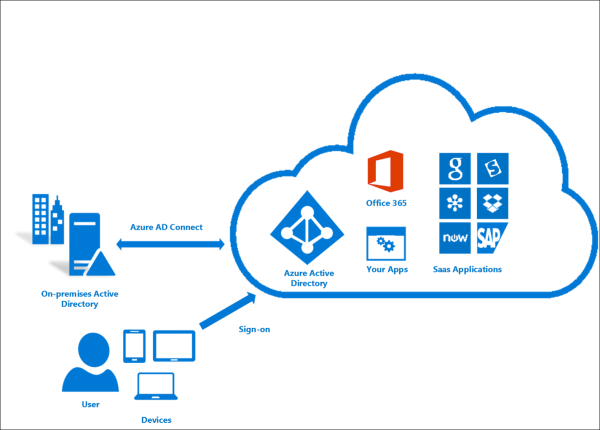
Merhaba arkadaşlar, Bu makalenin adını çok düşündüm tam olarak neyle açıklayacağımı bilemedim ama 1 gün bu sorun ile uğraştığımdan ipucu mahiyetinde yazmak istedim. ADSync ‘in ne olduğunu çoğumuz biliyoruzdur. OnPrem deki AD ile Office 365 gibi bir cloud servisini sync ...
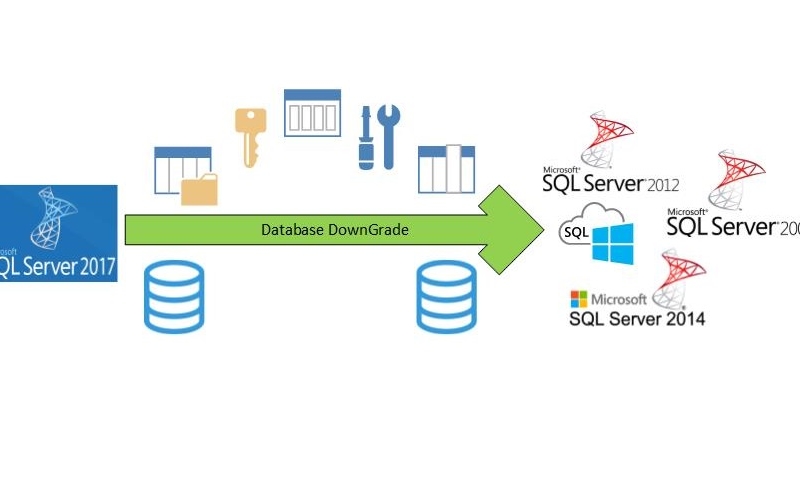
Merhaba arkadaşlar, Bugünkü konumuz SQL Server da alt versiyonlara database nasıl taşınır ondan bahsedip bir kaç kilit noktaya değineceğiz. Generate Script oluşturarak taşıma yapacağız ve kilit noktalara değineceğiz. Aslında işlem sorunsuz çalışmakta fakat DB boyutları belirli bir seviyenin üstünde olursa ...
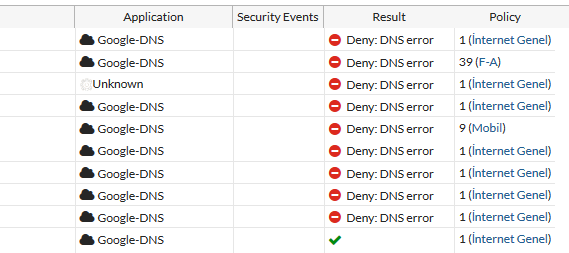
Herkese Merhaba, Fortios 5.4.1 ile gelen bir hatadan bahsedeyim. Bulunduğunuz ortamda internet yavaş şeklinde şikayetler alıyorsanız ve speedtest e girdiğiniz de Bant genişliğiniz kadar hız görebilirsiniz fakat speedtest yavaş geliyorsa yinede log lar alttaki gibi olacaktır. Action kısmında Deny:DNS error ...


Son yorumlar