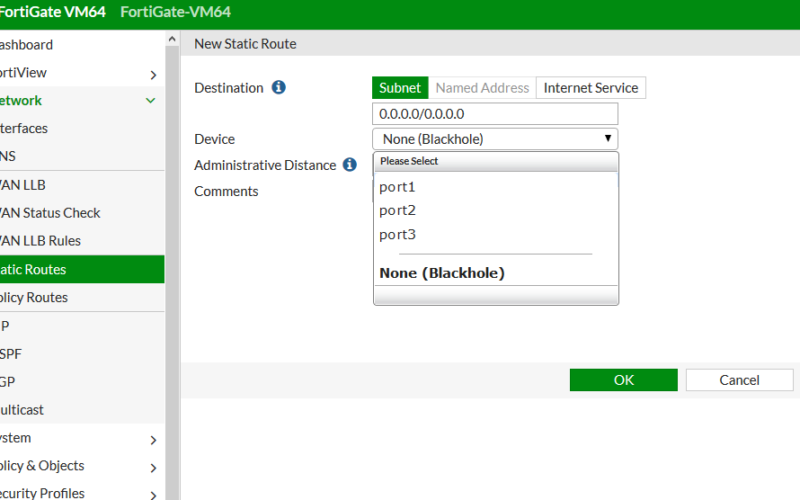
Herkese Merhaba, Bugünkü konumuz Black Hole ( Kara Delik) routing nedir, nerelerde kullanırız ve nasıl kullanırız gibi başlıklar altında anlatacağım. Black Hole Routing isminden de anlayacağınız gibi ( kara delik ) bir routing metodudur. Bu metodun temeli gelen saldırıları bir ...
Archives
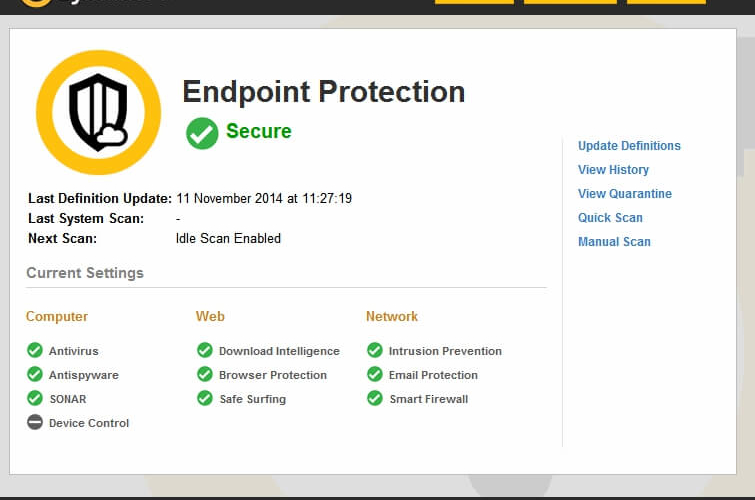
Herkese Merhaba, bugün SEP 14 (Symantec Endpoint Protection) Cloud uygulamasında Pending License Activation hatasının çözümünü anlatacağım. Öncelikle şunu belirteyim Cloud sürümünde client e yüklediğimizde bu hatayı alıyorsanız 4 saat e kadar düzelme ihtimali var yani hemen işlem yapmak zorunda değilsiniz. ...
Bu makalemde size ufak çaplı yeni Windows 10 un ilk ön izlenimini anlatmak istiyorum. Klasik Windows ve metro görünümle birleşmiş çok tatlı bir arayüz sunuluyor bize. Gerek görsellik gerek erişim açısından beklenilenin üstünde bir işletim sistemi. Not: Windows 10 ta ...



Son yorumlar