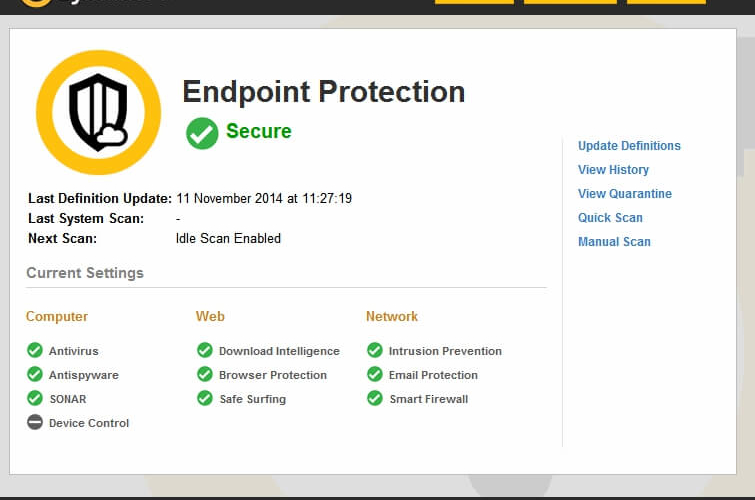
Herkese Merhaba, bugün SEP 14 (Symantec Endpoint Protection) Cloud uygulamasında Pending License Activation hatasının çözümünü anlatacağım.
Öncelikle şunu belirteyim Cloud sürümünde client e yüklediğimizde bu hatayı alıyorsanız 4 saat e kadar düzelme ihtimali var yani hemen işlem yapmak zorunda değilsiniz. İnternetten kaynaklı sebepleri de kontrol ettikten sonra alttaki işlemleri uygulamaya başlayabilirsiniz.
Bu hatayı aldığınız client da hiçbir koruma aktif olmaz ve admin arayüzde At Risk olarak işaretlenir.
Yapacağımız işlemler çok basit.
- İlk önce client makineden alttaki linkleri kontrol ediyoruz.
https://ins.spn.com
https://message.s2.spn.com
http://sasmain.symantec.com
http://sas1alt.symantec.com
https://ssaw.symantec.com
http://siaw.symantec.com
http://csasalt.symantec.com
eğer bu URL lere ulaşamıyorsa Firewall unuzdan bunlara izin vermeniz gerekmektedir.
- Bilgisayarı restart edip Güvenli Mod da başlatıyoruz.
-
Güvenli modda başlattıktan sonra alttaki klasörleri siliyoruz.
C:\ProgramData\Norton\00000083
C:\ProgramData\Norton\00000082
Program data gizli bir klasör olduğu için gizli klasörleri açmanız gerekir. Yada çalıştır a direk %ProgramData% yazarsanız klasöre ulaşabilirsiniz.
- Bilgisayarı restart edip normal şekilde başlatıyoruz.
Lisansın aktif olmuş olması gerekiyor. Eğer hala lisansınız aktif olmadıysa agent da secure ibaresini görmüyorsanız Agent ı kaldırıp tekrar kurmanız gerekmektedir.
İşinize yaraması dileğiyle.


Leave a Reply