Merhaba arkadaşlar,
Bugün Fortigate 5.47 build de LDAP Authentication nasıl yapılır onu anlatacağım. Adımları kısa tutup detaylara ağırlık vereğim.
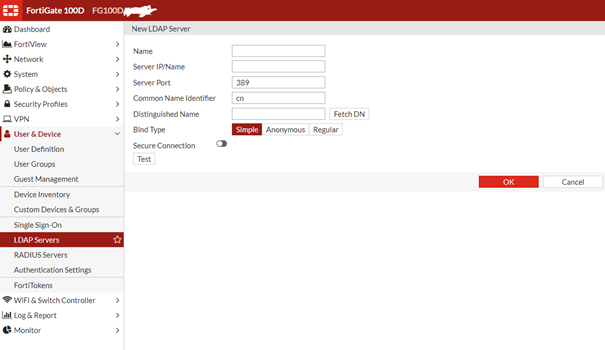
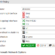
Menü den User & Device > LDAP Servers tabına geliyoruz. Ve Create New diyerek üstteki ekrana ulaşıyoruz. Bu ekranı alttaki gibi dolduruyorum.
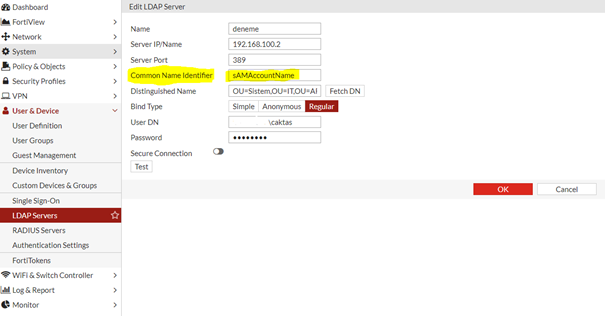
Şimdi burada gördüğünüz gibi bilgilerimizi doldurduk. Burada önemli olan tek nokta Common Name İdentifier I değiştirmemiz. Default ta CN geliyor biz ad deki kullanıcı adımızı alması için değeri görseldeki gibi değiştirdik. Ok diyip kaydediyoruz.
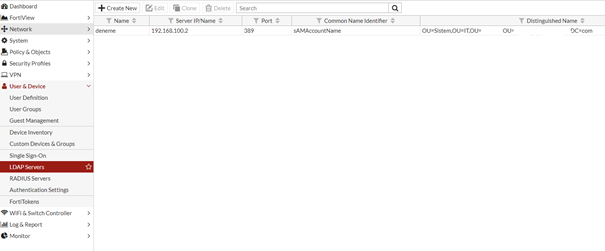
Tüm ayarları kaydettikten sonra görebiliyoruz. Ve şimdi LDAP tan bir kullanıcı oluşturuyoruz.
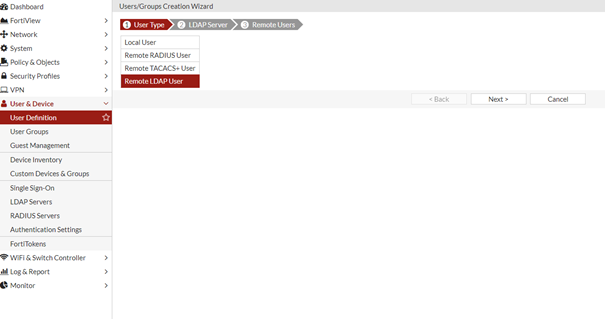
LDAP User I seçiyoruz.
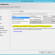
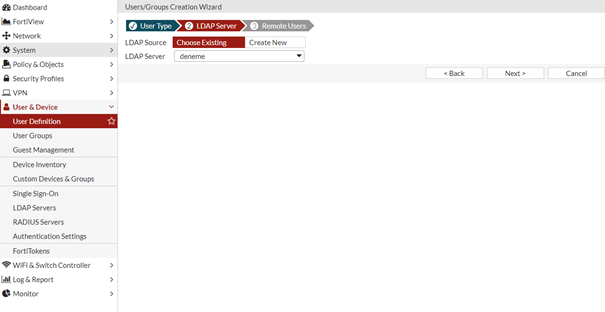 Choose Existing diyip oluşturduğumuz LDAP Server I seçiyoruz. Create New diyerek yeni bir ldap server eklersiniz.
Choose Existing diyip oluşturduğumuz LDAP Server I seçiyoruz. Create New diyerek yeni bir ldap server eklersiniz.
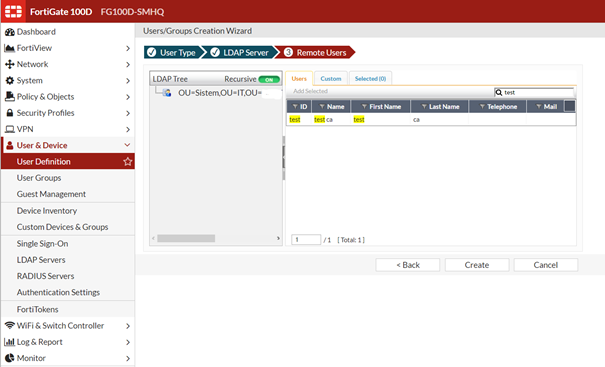
Gördüğünüz gibi test kullanıcımız burda. Üzerine 1 kere tıklayıp Add Selected diyoruz ve Create dediğimiz anda kullanıcımız oluşuyor.
Buraya kadar değineceğim bir detay yoktu, şimdi test edeceğiz ama test için logout olup ban yiyene kadar denemeyeceğiz J
diagnose test authserver ldap deneme test Aa123456
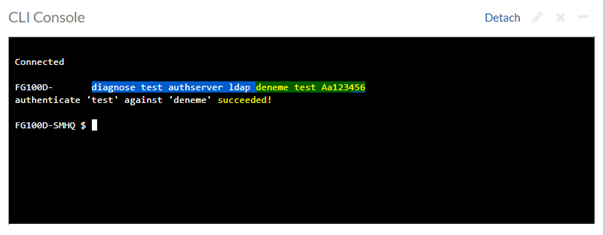
Komutta sarı ile işaretlediğimiz alanlar sırasıyla kurduğumuz LDAP Server Name – SAM – Password
Bunlardan öncesi zaten ana komutları olduğu için TAB yaparak da getirebilirsiniz.
NOT : LDAP dan gelen kullanıcıları admin olarak ekleyemezsiniz.


Leave a Reply